
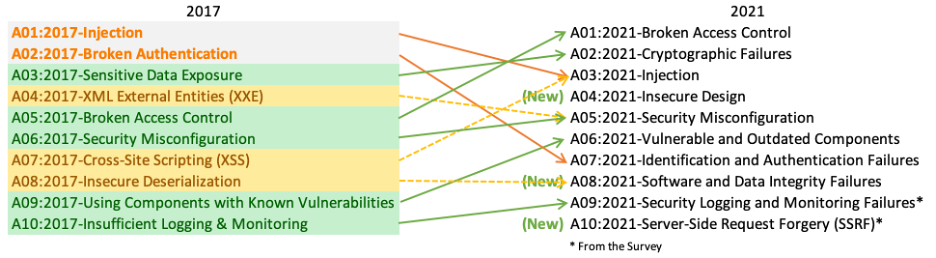
The OWASP Top 10 list is a list of the most critical web application security risks. It is compiled and maintained by the Open Web Application Security Project (OWASP).
The OWASP organization is an international non-profit group dedicated to improving the security of web applications. The Top 10 list is updated every three years, and the latest version was released in 2021.
The list provides a comprehensive overview of the most common and critical security risks that organizations should be aware of. The following is a breakdown of each of the items in the list currently with examples.
A01:2021 Broken Access Control
Highest in the list of the OWASP Top 10 vulnerabilities is Broken access control. Broken access control is when a user is able to access information or resources that they shouldn’t have access to. It can happen when an application does not properly restrict access to certain areas or resources. This can lead to a user being able to view, modify, or delete protected data.
This could include viewing or modifying other users’ accounts, or even deleting data. It is important for developers to ensure that their applications properly restrict access to certain areas and resources.
A02:2021 Cryptographic Failures
Next are Cryptographic failures. When we say cryptographic failures, we’re referring to errors in the implementation of cryptographic systems. These errors can lead to serious security issues and data breaches.
An example of a cryptographic failure is when an organization uses weak encryption algorithms. This means that hackers can easily decrypt the data and gain access to sensitive information.
“These errors can lead to serious security issues and data breaches”
Another type of cryptographic failure is when an organization does not properly store and manage cryptographic keys. This can lead to hackers gaining access to the keys and using them to decrypt data.
Finally, cryptographic failures can also occur when an organization does not properly implement cryptographic protocols. This can lead to hackers exploiting vulnerabilities in the system and gaining access to sensitive data.
A03:2021 Injection
Third in the list of OWASP Top 10 are Injection attacks. These attacks are a type of attack that occurs when malicious code is injected into an application. A block of code that is vulnerable can be used to access or modify data, or even execute commands.
Injection attacks are one of the most common web application security risks. SQL Injection is one example of an Injection attack. This is when a malicious user enters SQL code into a web form. If the web application doesn’t properly handle user’s input, then code can then be used to access or modify data in the database.
Developers can protect against Injection attacks by validating user input and using parameterized queries. Don’t forget that you need to validate your data server side. Anything that exists outside of the trust boundary can be bypassed.
“By properly handling user’s input developers can verify that only valid data is accepted, and that malicious code is not executed.“
Additionally, developers should use an up-to-date web application firewall to detect and block malicious code. Injection attacks are pretty serious. Companies can mitigate risk by ensuring their engineers are conducting quality code reviews.
By conducting good code reviews, validating user input, and using a web application firewall, developers can protect their applications from malicious code injection.
A04:2021 Insecure Design
Insecure design is a broad concept that involves weaknesses in the design of controls. OWASP defines it as “missing or ineffective control design”.
Insecure design is not the source for all other Top 10 risk categories. There is a difference between insecure design and insecure implementation.
OWASP A04:2021 https://owasp.org/Top10/A04_2021-Insecure_Design/
A04:2021 of the OWASP Top 10 isn’t just about implementing something that becomes vulnerable or is vulnerable. It starts with the design of the architecture, because bad designs can’t be fixed with a perfect implementation. It’s just a good implementation of a bad idea.
A05:2021 Security Misconfiguration
Next in the OWASP Top 10 is A05:2021, Security misconfigurations. Security misconfigurations are usually mistakes made by system admins or developers when setting up or modifying a system or application.
“Security misconfigurations are usually mistakes made by system admins or developers”
Here is an example of a security misconfiguration.
Consider a system administrator sets up a web server with default settings. When this is done, it leaves the server vulnerable to attack because the default settings are not always the most secure settings.
Another example is allowing all applications on a Linux machine to run as root. A better way to approach this would be to limit an application to the privileges it needs to do its job and nothing more.
Companies should be reviewing their security configurations regularly. This will mitigate the risk that something was updated incorrectly and left an opening for attack.
A06:2021 Vulnerable and Outdated Components
Let’s talk about A06:2021 – Outdated Components. These are components of software that have known security vulnerabilities or are outdated.
There are many examples of outdated components. It could be your OS, your browser, a library that an application you have installed uses. The list is endless and honestly it makes identifying this one very difficult. Companies that produce software are particularly at risk because developers tend to install all types of software on their machines.
From an organizational perspective, an IT department should regularly check for vulnerable and outdated components in their software as well as scan their employee machines and update them as soon as possible. This will help protect their systems from malicious actors and ensure their data is secure.
A07:2021 Identification and Authentication Failures
Identification and Authentication Failures are security issues related to the process of identifying and authenticating users. This process is important for ensuring that only authorized users can access a system or application.
Identification is the process of recognizing a user, while authentication is the process of verifying the user’s identity.
An example of an Identification and Authentication Failure is a weak password. If a user chooses a password that is too simple, it can be easily guessed or cracked by malicious actors. This can allow unauthorized access to the system or application, leading to a security breach.
“This can allow unauthorized access to the system or application, leading to a security breach“
Another example of an Identification and Authentication Failure is a lack of multi-factor authentication. This is when a user is only asked to provide a single form of authentication, such as a username and password.
Multi-factor authentication requires users to provide multiple forms of authentication, such as a username, password, and a one-time code sent to their phone. This adds an extra layer of security to the authentication process.
A08:2021 Software and Data Integrity Failures
Software and data integrity failures can occur when an application relies on plugins, libraries, or modules from untrusted sources. An insecure CI/CD pipeline can also introduce the potential for unauthorized access, malicious code, or system compromise.
Something else to consider is auto-update functionality. This can be vulnerable to attack as well. When updates are applied without verifying that the update is safe, then auto updates can be used to distribute an attacker’s code directly into your pipeline.
A09:2021 Security Logging and Monitoring Failures
Security logging and monitoring is an important part of cyber security. It rose slightly from the tenth position in the OWASP Top 10 2017 to the third position in the Top 10 community survey.
This type of security can be difficult to test, often requiring interviews or asking if attacks were detected during a penetration test. There is not much CVE/CVSS data available for this category, but it is essential to detect and respond to breaches.
Security logging and monitoring can be very beneficial for accountability, visibility, incident alerting, and forensics. This category includes CWE-778 Insufficient Logging, CWE-117 Improper Output Neutralization for Logs, CWE-223 Omission of Security-relevant Information, and CWE-532 Insertion of Sensitive Information into Log File.
It is important to have the right measures in place to ensure the security of a system.
A10:2021 Server-Side Request Forgery
SSRF is a serious security vulnerability that can be used to gain access to internal systems, bypass firewalls, and even launch DDoS attacks. To prevent SSRF, developers should validate user-supplied URLs and use secure authentication methods.
Example: SSRF flaws are becoming more common as web applications provide users with convenient features.
These flaws occur when a web application fetches a remote resource without validating the user-supplied URL. This allows an attacker to manipulate the application to send a crafted request to an unexpected destination, even when protected by a firewall or VPN.
“SSRF flaws are becoming more common as web applications provide users with convenient features.”
The severity of SSRF is increasing due to cloud services and the complexity of architectures. To protect against these threats, developers must validate user-supplied URLs and use secure authentication methods.
SSRF is a serious security vulnerability that can have devastating consequences. It is important for developers to be aware of the risks and take steps to prevent it. This includes validating user-supplied URLs, using secure authentication methods, and monitoring for suspicious activity.
Some of this article was automatically generated by the Open AI platform and then modified by the author to include headers, editing, formatting and personal experience. The human author takes responsibility for everything said here as well as its accuracy

